Introduction
The European Blockchain Services Infrastructure (EBSI) is building an ecosystem for issuing and verifying digital credentials. Within this ecosystem, multiple key actors must exchange information securely and efficiently. However, the nature of this data varies depending on the specific use case.
So, how does this end-to-end communication work? How is the journey from credential issuance to verification completed seamlessly? The answer lies in a well-integrated family of standards.
By working closely with real-world use cases, EBSI has developed a framework that ensures secure and reliable credential exchange. This article explores the essential standards and protocols that enable this framework and how they interact at each stage, ensuring smooth interoperability across different technologies.
The Challenges: Why Do We Need Standards?
With so many actors exchanging data, ensuring security, reliability, and interoperability presents significant challenges:
- Data Integrity and Trust: Credentials must be tamper-proof and verifiable.
- Interoperability: Different systems must communicate seamlessly across borders and industries.
- Privacy and Selective Disclosure: Users must have control over which parts of their credentials are shared.
- Decentralization and Security: Centralized verification systems introduce risks and single points of failure.
These challenges highlight the necessity of adopting standardized frameworks to ensure smooth and secure credential exchanges.
Key Standards in the framework
EBSI leverages several key standards and protocols to ensure the secure issuance and verification of credentials. According to their function, we could group them as follows:
To help standardise the credential and its structure:
- Verifiable Credential Data Model (VCDM) by W3C: Data model.
- JSON Schema: Structure
- JSON-LD (Linked Data): Semantics for multi-language support.
To help standardise the issuance and presentation:
- JWS (JSON Web Signature): Ensures the integrity and authenticity of the data.
- JAdES (JWS extension, adding additional features to meet the requirements of advanced electronic signatures such as timestamps and signature policies.)
- OpenID Connect: Adds authentication capabilities to OAuth 2.0, enabling user identity verification.
- OpenID4VCI: Issuing credentials
- OpenID4VP: Presenting Credentials
- For the cases of Selective Disclosure
- JWT-SD (JSON Web Token Selective Disclosure): Allows selective disclosure of credential information.
To help securely and uniquely identify the different actors:
- DID (decentralised Identifiers): Provides an unique and decentralised method for identifying entities.
The Stages of E2E Information Flow
The end-to-end (E2E) information flow in EBSI involves three key stages to ensure the secure issuance and verification of credentials.
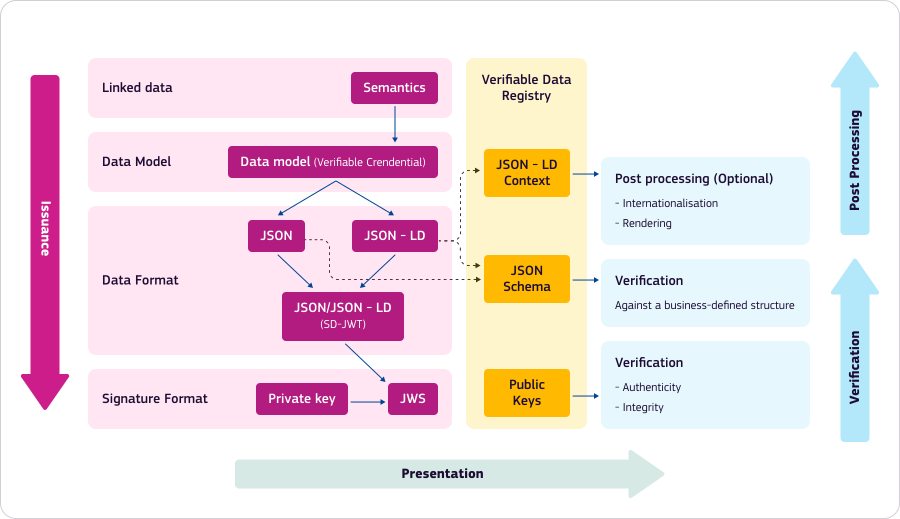
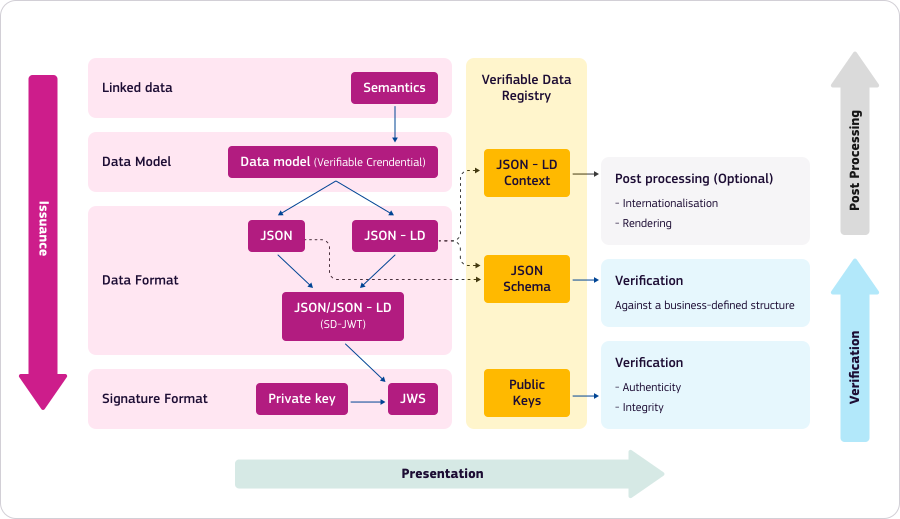
Stage 1: Issuance - Creating Secure Credentials
As an Issuer, how do I issue Verifiable Credentials?
Defining the Data Model
To issue Verifiable Credentials, we must first define the data model. The core data model adheres to the W3C Verifiable Credentials Data Model standard. Use cases further specify their data model and the data structure is expressed using the JSON Schema standard. Use cases that require linking vocabularies to their data model follow the W3C JSON-LD standard. Additionally, for multi-language support, the i18next standard is widely used. Once the data model is defined and approved for a use case, it is published in the EBSI Trusted Schemas Registry.
Becoming a Trusted Issuer
To make Verifiable Credentials trustworthy, we need to know whether the issuing organisation is entitled to issue the Verifiable Credentials. This is achieved by organisations becoming Trusted Issuers in the EBSI’s Issuer Trust Framework. For organisations to become Trusted Issuers, they need to request their Verifiable Accreditation that are expressed using the W3C Verifiable Credentials data model. Organisations can easily request Verifiable Accreditations and present the required Verifiable Credentials using the OpenID for Verifiable Credential Issuance and OpenID for Verifiable Presentations. All the accreditation and signing keys are linked via Decentralized Identifiers following the W3C Decentralized Identifiers standard.
Identifying the users
Before issuers issue Verifiable Credential to users, they need to identify them. Identification is in the domain of the issuer and the issuer can define identification and authentication means that meet their identification and security requirements. When cross-border interactions are taking place, organisations rely on the eIDAS regulation, whereas authentication is in many cases implemented using the OIDC or SAML protocol.
Preparing the Verifiable Credential
Before the Verifiable Credentials are issued, issuers must populate the missing data from their database (or manually), they need to decide on the revocation mechanism where they can rely on the EBSI Revocation Framework. Whenever Verifiable Credentials are bound to digital wallets, the holder decentralised Identifier is added to the Verifiable Credential. Issuers also need to attach their Verifiable Accreditations according to the EBSI Trust Framework. Use cases that support selective disclosure, transform the credentials so that holders can selectively disclose certain claims, following selective disclosure standards, such as SD-JWT. If I need to express claims in different languages, I’m relying on the JSON-LD internationalisation framework
Signing the Verifiable Credentials
Once the Verifiable Credentials contain all the information, they can be signed. Signature formats follow the JSON Web Signature standard, and for legal recognition, use cases are relying on the eIDAS regulation and are integrating the JAdES signature profiles.
Delivering the Verifiable Credentials to Wallets
Once the Verifiable Credential is issued, it is delivered to the holder’s wallet according to the OpenID for Verifiable Credentials Issuance standard. If additional information about the wallet is required, prior to the issuance, OpenID for Verifiable Presentations is used.
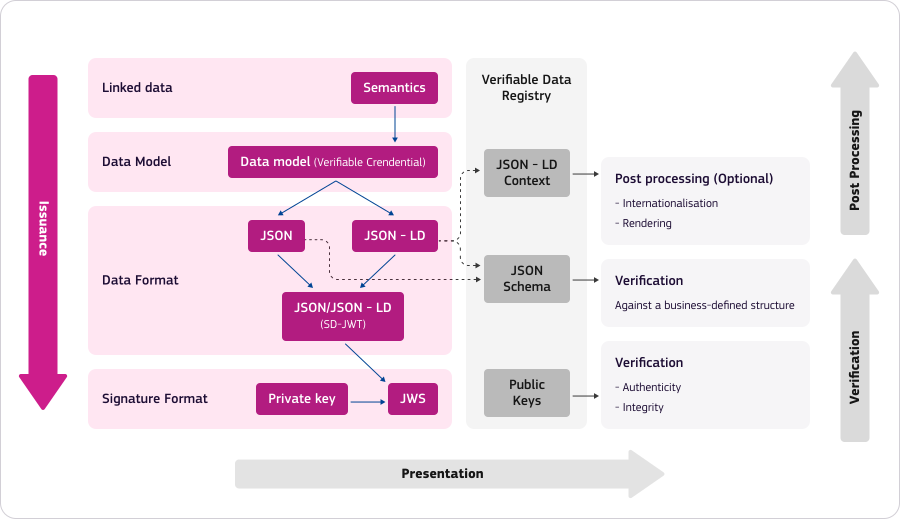
Stage 2: Presentation - Creating and Issuing Verifiable Credential Presentation
Now that I, as a holder, have my credentials in my wallet, I can present them to the different Verifiers.
Verify the Verifier
Whenever I’m sharing critical data, it’s crucial to ensure that the Verifier is not over-asking and that the Verifier is entitled to request the information. For that, EBSI Verifier’s Trust Framework is used. In open-sharing scenario, this step is optional.
Create a presentation
Once I’m ready to share my Verifiable Credentials, I decide which claims I’m about to disclose and my wallet derives the disclosures according to the IETF SD-JWT selective disclosure. Next, I create a W3C Verifiable Presentation, and sign it. Next, I present my Verifiable Presentation via the OpenID for Verifiable Presentations protocol.
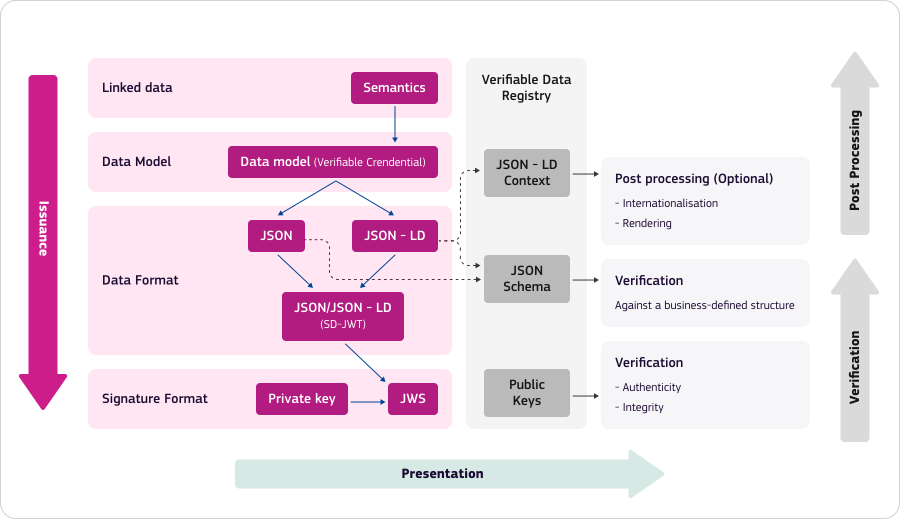
Stage 3: Verification - Ensuring Trust and Authenticity
As Verifier, I receive Verifiable Presentations via the OpenID for VP protocol. Once I receive the Verifiable Credentials, I rely on numerous standards to perform independent verification:
- EBSI Issuer Trust Model to verify the identity and authorization of the issuer
- JWS and JAdES to verify the digital signature
- eIDAS regulation to verify the identity of the signer
- W3C Verifiable Credentials Data Model to verify the content
- JSON Schema to verify the structure
- JSON-LD to check the vocabulary
- EBSI revocation framework to check the Verifiable Credential status
If I need additional information from the user, I use OpenID for Verifiable Credentials to ask for other claims.
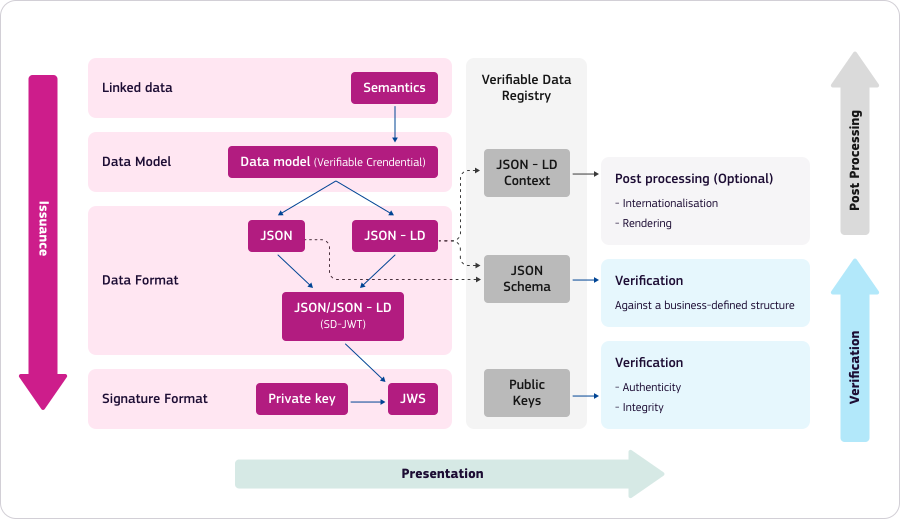
The Verifiable Data Registry
The Verifiable Data Registry acts as a trust anchor in the EBSI ecosystem. It stores the DID documents containing the public keys of all trusted entities, along with their accreditations, and also stores the trusted JSON schemas, allowing verifiers to confirm the integrity and authenticity of the credentials. This registry is built on a blockchain network, which offers several key benefits:
- Decentralization: Unlike a centralized authority, the blockchain does not rely on a single part that could be a single point of failure, enhancing the system's resilience and reliability.
- Ease and Speed of Validation: The decentralized nature of blockchain allows for quicker and more efficient validation and verification processes.
- Historical Record: Blockchain technology maintains a historical record of transactions, providing a transparent and auditable trail.
- Security: The immutability of blockchain records ensures that once data is recorded, it cannot be altered, adding a layer of security.
- Consensus Protocol: The consensus mechanism used in this decentralized network ensures that all participants agree on the validity of transactions, making the system secure and trustworthy.
How is this trust generated? In EBSI, identities, permissions, and accreditations of actors can be stored and retrieved, allowing anyone to verify the information anytime. The system acts as a notary based on rules agreed upon by the ecosystem.
Real-World Applications
Exists numerous real-world applications. For example, universities can issue digital diplomas that graduates can store in their wallets and present to employers. Similarly, government agencies can issue digital IDs that citizens can use to access public services securely. As an illustration, the following scenario can be considered:
- Issuance (Issuer): A university issues the diploma in a Verifiable Credential format (OpenID4VCI). The data is signed with JWS (JSON Web Signature) to ensure security and integrity.
- Presentation (Holder): The user decides which claims are disclosed (IETF SD-JWT), creates the Verifiable Presentation (W3C VP), and signs it (JWS). Afterward, the user presents the VP (OpenID4VP)
- Verification (Verifier): When the user applies for a job by issuing the VP, the employer (verifier) relies on numerous standards to perform the verification. Retrieving information stored in the Trust Registry, the employer confirms the integrity, authenticity and validity of the diploma.
Conclusions
The journey of issuing, signing, presenting and verifying a credential within EBSI is possible due to the role of many the standards that ensure a secure, interoperable, and user-centric approach. This standards, work in harmony on several moments of the process as it can be illustrated on the sequence diagram below.